Clear Linux, as is mentioned on the project's website as one of its standout design features, places a priority on security, considering it in its core design instead of as an additional consideration outside and after the core design.
Introduction
Clear Linux places a priority on security, considering it in its core design instead of an addition outside the core.
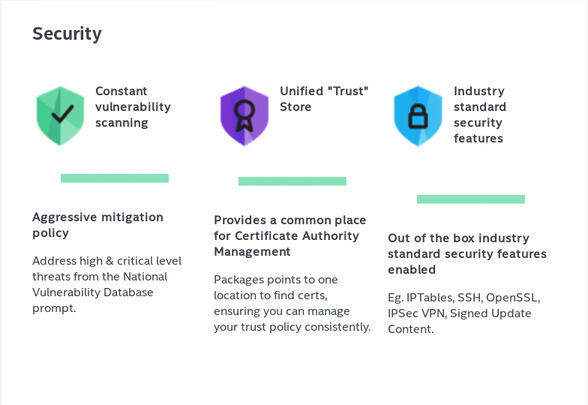
Infographic from the Clear Linux Website Showing Some Security Features
Security Features
Below are some of the features highlighted on the project's website.
-
frequent updates of at least one and up to two per day to incorporate upstream security upgrades and security patches as soon as they are available
-
the latest Linux kernel codebase to incorporate the newest features, as well as the latest security fixes
-
a rolling release model with automatic updating (overridable) that includes tools to restart services as needed (configurable)
-
proactive scanning of packages against repositories of Common Vulnerabilities and Exposures (CVEs) as published by NIST to ensure security patches are appled as soon as possible
-
minimized attack surface by removing legacy, unneeded, and redundant standards and software as well as those theat expose sensitive system information
-
uses encryption and signature verification in update processes, in build processes to include verification of third party software, and includes a tool to centrally manage certificates
-
software components are built with secure options, the kernel is signed and incorporates kernel features to mitigate memory based attacks and verify the integrity of storage devices
-
full disk encryption, password hardening tools, and SSH login monitoring and blocking are available
Other Security Features
Like the most security conscious distributions, openSUSE and Fedora, Clear Linux requires authentication when accessing external partitions on the same computer. But unlike these, or any other distribution, Clear Linux also requires authentication when connecting an external USB storage device.
Considerations
Some of the security features combined with the lack of certain widely used software may require users to build and install third-party kernel modules. In my case, in order to use VirtualBox, I had to install the generic version downloaded from the VirtualBox site. -- downloaded from the VirtualBox site, which requires certain kernel modules distributed by VirtualBox. As the kernel and all kernel modules are verified by the Clear Linux OS, building the VirtualBox modules fails during VirtualBox installation.
-
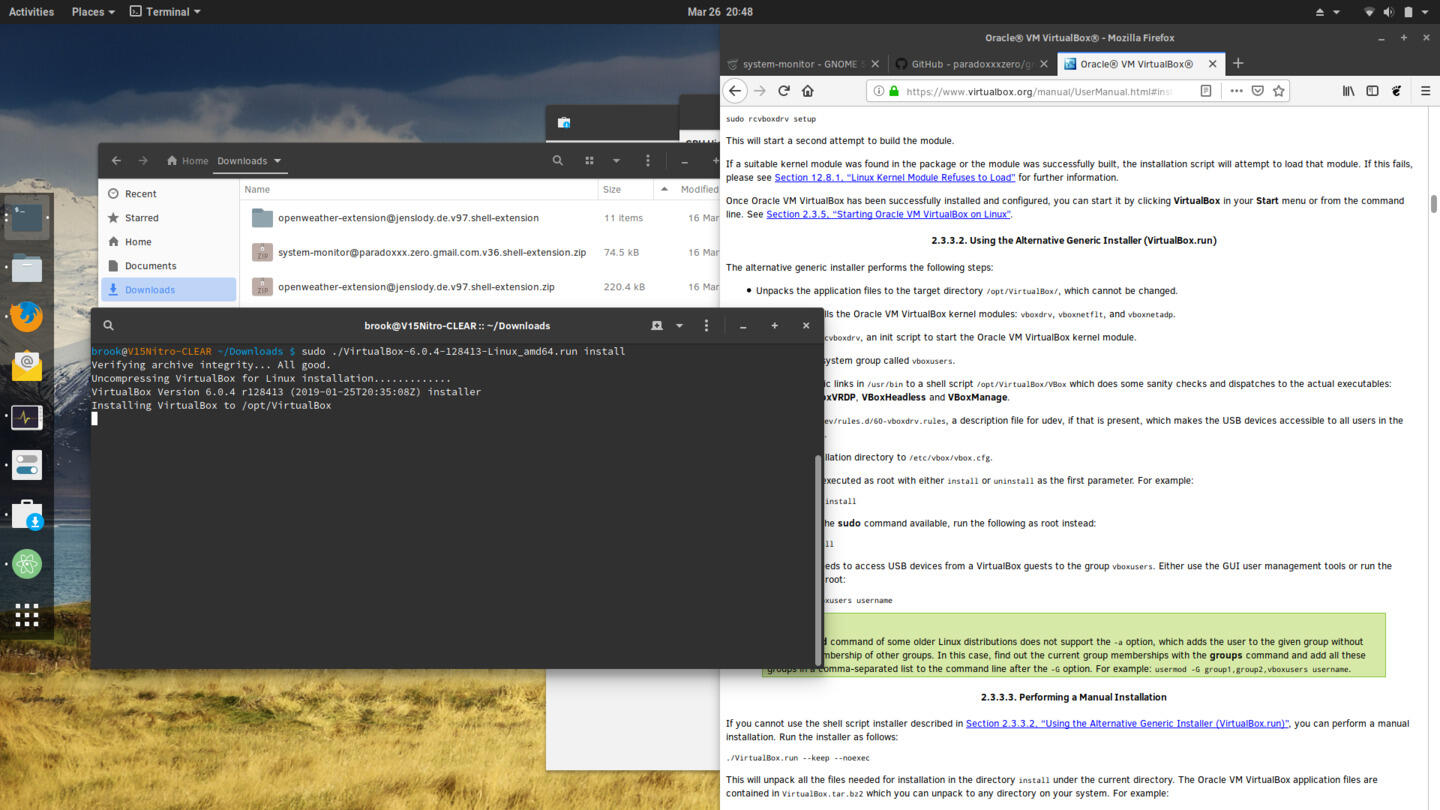
Installing VirtualBox
-
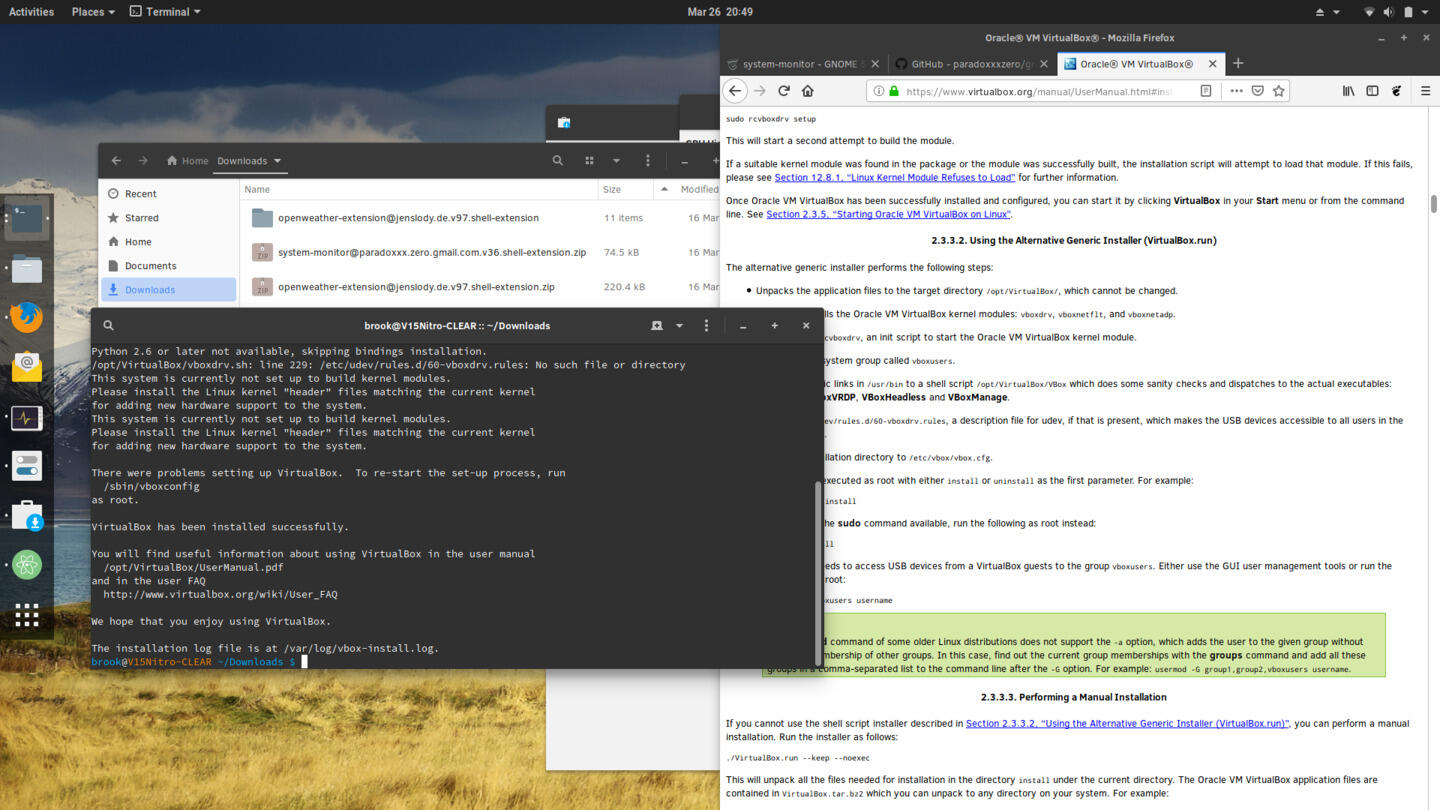
Installing VirtualBox
-
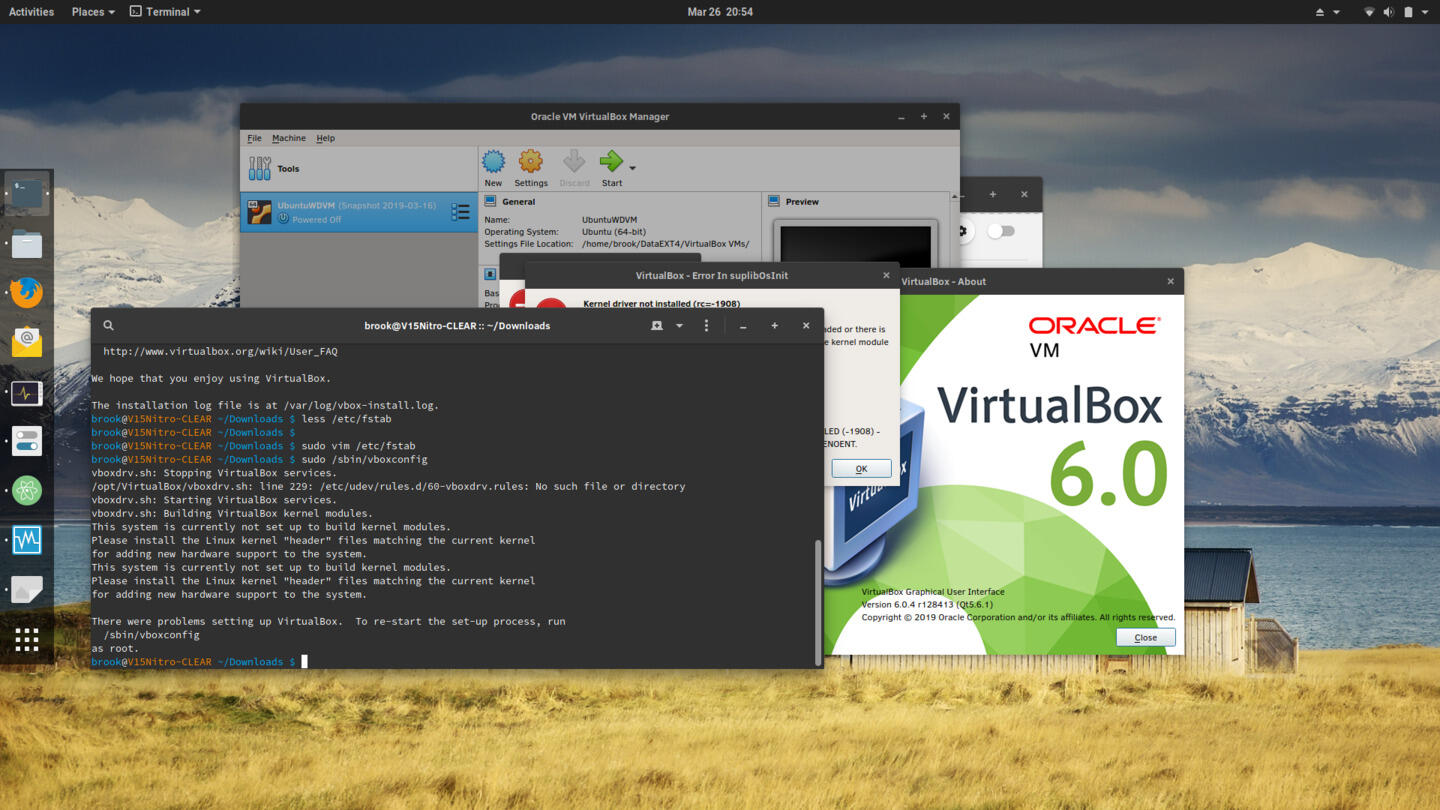
Installing VirtualBox
Attempting to Build Third Party Kernel Modules Fails
Because Clear Linux enforces signature verification of the kernel module even with SecureBoot disabled, third-party modules can't be built and included in Clear Linux, without configuration changes.
In order to use third-party kernel modules, it is possible to disable enforcement of kernel signature verification by including module.sig unenforce in the file /etc/kernel/cmdline.d/allow-unsigned-modules.conf and running sudo clr-boot-manager update
sudo mkdir -p /etc/kernel/cmdline.d
echo "module.sig_unenforce" | sudo tee /etc/kernel/cmdline.d/allow-unsigned-modules.conf
sudo clr-boot-manager update
sudo reboot